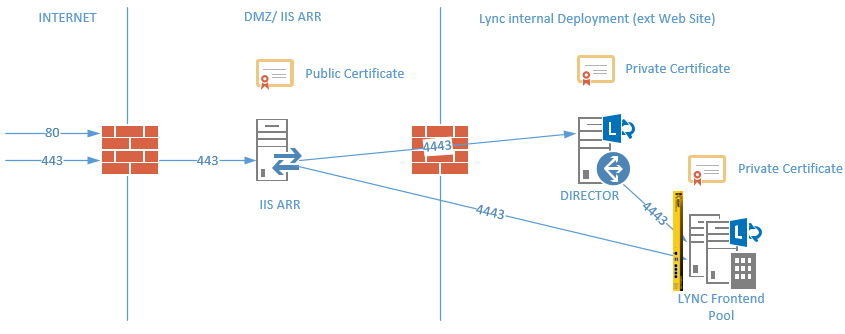
Certificate requirements for internal Lync servers
Lync is quiet strict in certificate validation. If you assign a non compatible certificate to Lync it will run into serious issues. This is most likely happen if you are using dedicated certificate for each Lync service. Especially the Lync WebServiceInternal certificate cannot be requested correctly, neither with Lync Wizard nor with the Request-CsCertificate command. Here the problem is that both methods are requesting a certificate with a Subject Name of the Internal Web Services rather than the POOL FQDN. Lync BUG: The remote certificate is invalid according to the validation procedure. reason="The web ticket is invalid." ;faultcode="wsse:InvalidSecurityToken",Replace=false In both, the TechNet and Help File the correct certificate is described. Therefore you need a valide process of requesting the correct certificate. If you have a consolidated certificate for all services, this is issue is not present, because the Subject Name responds to the POO...